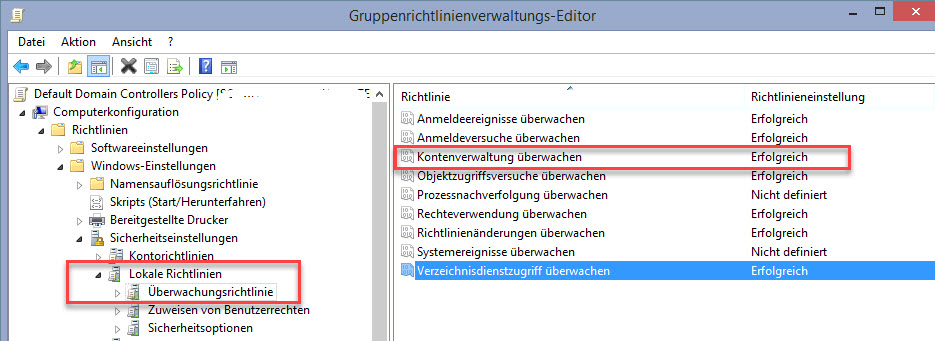
Aktivieren der Überwachung am Domänen Controller und protokollierem im Eventlog.
Folgende Schritte ausführen, um bestimmte Ereignisse zu überwachen:
- Gruppenrichtlinien Management Console starten (Start-Process $env:systemdrive:\windows\system32\gpmc.msc)
- Default Domain Controllers Policy wählen
- Rechts Klick Bearbeiten
- Navigiere zu Computerkonfiguration --> Richtlinien --> Windows Einstellungen --> Sicherheitseinstellungen --> Lokale Richtlinien -->Überwachungsrichtlinie
- Überwachungsrichtlinie doppelklicken und im rechten Fenster die gewünschten Einstellungen auswählen und konfigurieren
- Domänen Controller neu starten
Ereignis IDS bei der Kontoverwaltungsüberwachung: (S=Success, F=Fail)
4720 (S): A user account was created.
4722( S): A user account was enabled.
4723 (S, F): An attempt was made to change an account's password.
4724 (S, F): An attempt was made to reset an account's password.
4725 (S): A user account was disabled.
4726 ( S): A user account was deleted.
4738 ( S): A user account was changed.
4740 ( S): A user account was locked out.
4765 (S): SID History was added to an account.
4766 ( F): An attempt to add SID History to an account failed.
4767 (S): A user account was unlocked.
4780 (S): The ACL was set on accounts which are members of administrators groups.
4781 (S): The name of an account was changed.
4794 (S, F): An attempt was made to set the Directory Services Restore Mode administrator password.
4798 (S): A user's local group membership was enumerated.
5376 (S): Credential Manager credentials were backed up.
5377 (S): Credential Manager credentials were restored from a backup.
Quellen: https://docs.microsoft.com/en-us/windows/device-security/auditing/audit-user-account-management